7 Common Information Security Myths
posted by John Spacey, February 14, 2011Information security is a widely misunderstood topic. These security myths are so common that even some security experts fall for them.
1. Security vulnerabilities are inherently bad and need to be eliminated
'Security Vulnerability' sounds like a bad thing. However, consider this — employees accessing the Internet, answering the phone and using productivity software are all security vulnerabilities.Sure, some vulnerabilities are bad — no organization needs a software bug or dishonest employee. However, organizations need to be open, connected and responsive to change — vulnerabilities are part of doing business.
A company may decide that employees need to access the Internet and have mobile phones — even though these activities expose the company to security vulnerabilities. In other words, many vulnerabilities (such as the Internet) are bad from a security perspective and good from a business perspective.
Information security is about eliminating some vulnerabilities and mitigating others.
2. Vulnerabilities are threats
Security experts, commentators and the media often confuse the two most important words in the security vocabulary: vulnerability and threat.A statement such as "mobile phones represent a security threat" is technically wrong. After all, when is the last time a mobile phone threatened you? From a security point of view, there is a big difference between a vulnerability and a threat.
Threats are people, technology or events that have potential to cause information security incidents. Examples: viruses, the press, angry employees, natural disasters
Vulnerabilities are openings that can be exploited by threats. Example: software bug, human error, mobile phones etc...
3. Information security is a software problem
When most people think about information security they think about software bugs, viruses and other software related risks.The fact is that information security incidents often have little or nothing to do with software:
- a partner who accidentally releases top secret product plans to the press.
- an employee who loses a briefcase at a nightclub.
- a sales person who accidentally emails a price-list to a competitor.
- a earthquake that destroys a data center.
- a war that disrupts satellite communications.
Information security risks include software, equipment, business, human, political, and natural factors.
4. Human error = laziness
Some security professionals refer to 'lazy and incompetent employees' as being the primary source of human error. This is just plain wrong.The fact is that perfectly diligent and competent employees can have a high error rate. The source of human errors is deeply engrained in the way humans perceive the world, communicate, socialize and react to events.
Effective management and training techniques can drastically reduce human error.
5. Don't worry, the audit will fix it
Most large organizations undergo regular security audits such as ISO 27001 certification. It is common to believe that certification means the organization has fixed its security problems.There are numerous reasons this is generally not true:
1. Scope of audits can be limited — excluding systems or entire business units.
2. Audits often involve brainstorming lists of vulnerabilities — these lists are rarely complete.
3. Audits generally seek to establish controls to mitigate vulnerabilities — often controls are ineffective.
6. Management's responsibility ends with assigning some security experts
Managing information security requires participation from executive management, business management, IT management, working level staff, partners, suppliers and customers. It is naive to think that a few experts can go off in a room somewhere and solve the company's security problems.7. Don't worry, security patches will fix it
Often security patches are too late to protect the organization from threats. In fact, vulnerabilities are often discovered due to security incidents.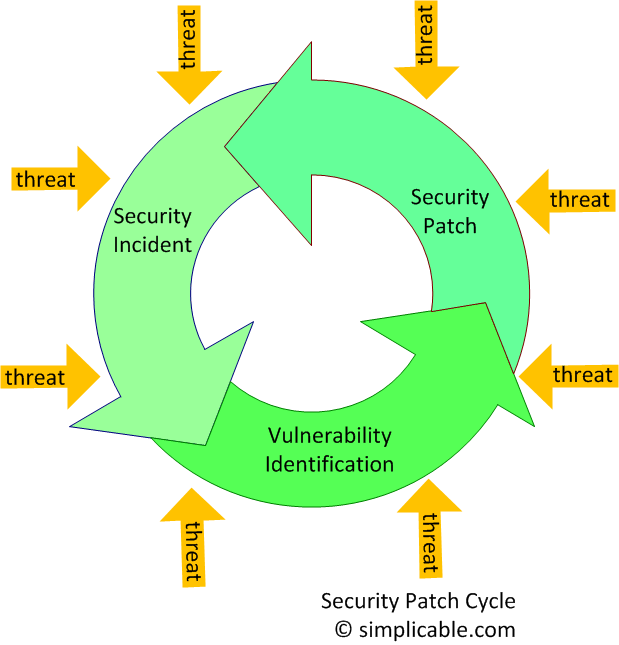
Recently on Simplicable

| The Difference Between Public, Private and Hybrid Cloudposted by Anna MarPopular ideas such as cloud computing get twisted, turned and flipped upside down before anyone can agree on common definitions. |

| 5 Levels of Tech Savvy Blissposted by Anna MarModern technology customers and industry insiders are faced with a constant stream of change. Human ability to adapt to this pace of change is remarkable. |

| The 20 People In Your Organization Who Need Enterprise Architectureposted by Anna MarEnterprise architects are leaders. They're near the top of the technical food chain in any organization. As leaders, there are a lot of people in the organization EAs can help. |



















