A Simple Process for Enterprise Architecture Governance
posted by John Spacey, April 23, 2011A simple reference process for EA project governance. The process works well — but requires support from the CIO, PMO and operations.
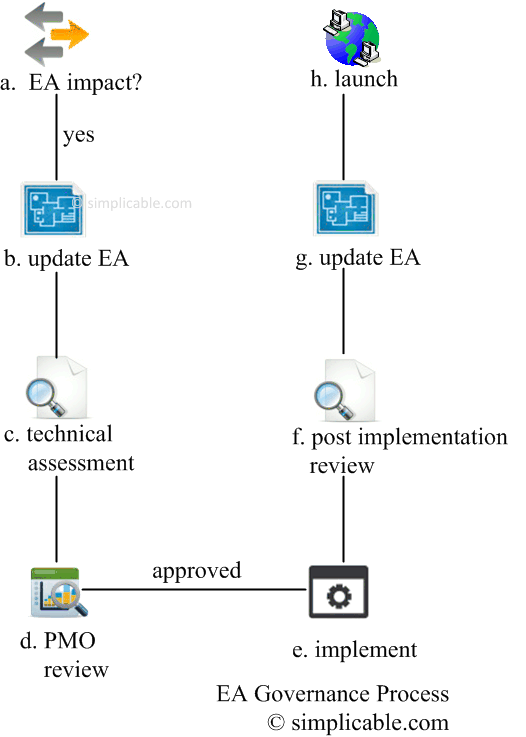
a. EA impact?
EA governance is too heavy for small, non strategic projects. Inclusion criteria typically considers both project budget and strategic impact.b. update EA
Make sure that future looking components of the EA such as gaps, strategy and transition architectures reflect the project.c. technical assessment
The EA team reviews the project — this should include the project charter and macro design. Action items must be addressed before proceeding to the PMO review.d. PMO review
The project management office (PMO) reviews the project including the business case, budget and other initiation phase items.e. implement
The implementation team is responsible for compiling with the macro design and enterprise architecture.f. post implementation review
The EA team reviews the work of the implementation team. Action items need to be addressed before launch.g. update EA
The current state EA is updated to reflect the project.h. launch
Governance has ensured that the project launched into production conforms with the EA and is reflected in EA documentation.Recently on Simplicable

| Cloud Guideposted by John SpaceyA guide to cloud computing including cheat sheets, best practices and metrics. |

| Web Security: Battleships and Locustsposted by Anna MarThere are two types of web security threats: battleships and locusts. |

| Web Security Illustratedposted by John SpaceyHow would you explain web security to your grandmother? |



















