Disrupting the Spam Value Chain
posted by Anna Mar, May 31, 2011A group of 15 university researchers has done a interesting study of the spam value chain — how spam gets converted into cash.
The Spam Value Chain
The researchers were able to track 365 million URLs from spam messages back to 45 affiliate programs.The researchers also made 120 purchases from spammers and then followed the money. The result: 95% of the spam payments flowed through 14 banks such as Azerigazbank in Azerbaijan and Wirecard AG in Germany.
Recommendations: Stop Paying Spam's Bankers
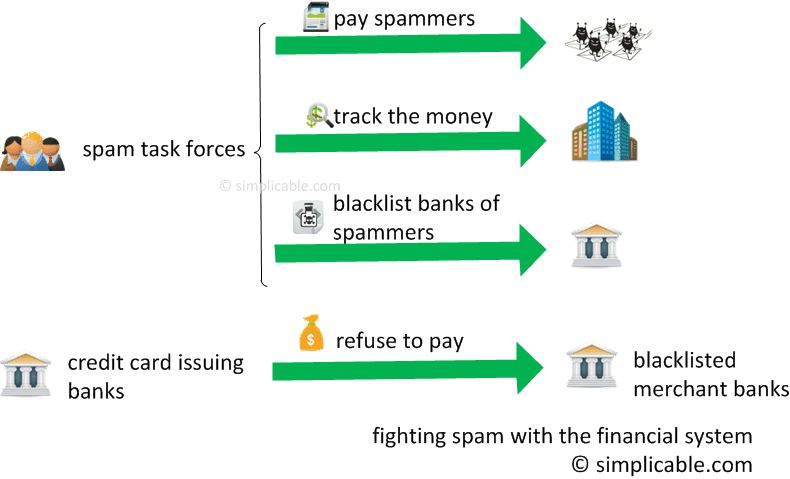
The researchers suggest that current anti-spam strategies such as attacking botnets and spam filtering are ineffective. Spammers can quickly recover from lost botnets — and filtering will never be 100% effective.They suggest the best way to stop spam is to go after the money:
- establish a task force that makes spam purchases and follows the money to merchant banks.
- identify the merchant banks where most spam money is flowing and blacklist them.
- refuse to settle credit card transactions for blacklisted banks.
Blacklisted banks would presumably be able to apply to get off the blacklist by freezing the accounts of spammers and strengthening their know-your-customer processes.
Existing Laws
It is not such a stretch to make banks responsible for the acts of their clients. There are already well establish international banking laws that do just that — including anti-money laundering and know-your-customer regulations.The Internet is an easy place to hide — Internet resources can be obtained quickly and anonymously. Money on the other-hand is highly traceable. A similar approach can no doubt be taken to deal with malware.
Survey

|
Current state blueprints capture business, data and implementation architecture at the conceptual, logical and physical levels. |
Recently on Simplicable

| IT Security Guideposted by John SpaceyA guide to information security including cheat sheets, best practices and checklists. |

| Authentication vs Authorizationposted by Anna MarIt is easy enough to confuse authentication and authorization. |


















