Information Security Management in 90 Seconds
posted by John Spacey, February 13, 2011Information Security Management (ISM) is an increasingly important part of corporate governance. In fact, most large companies are now legally required to report their information security status to shareholders (ie. Sarbanes-Oxley Act of 2002 etc..).
What is Information Security?
Information Security ensures data confidentiality, control, integrity, authenticity, availability and utility.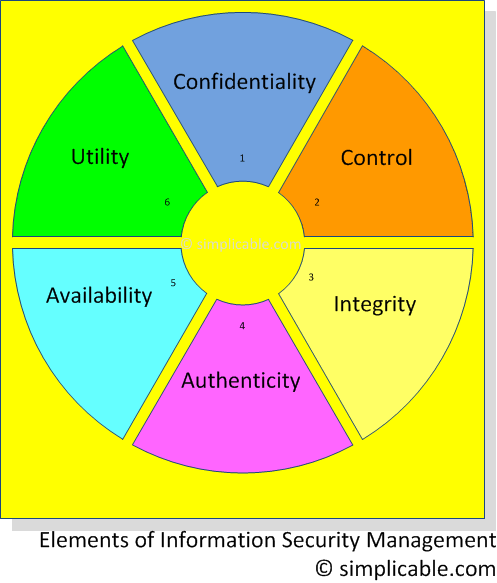
Confidentiality
Restricting access to data. Example: new product designs should be hidden from competitors.Control
Possession of data. Example: loss of a corporate laptop — if the hard drive is encrypted confidentiality has been maintained but control has been lost.Integrity
Data correctness. Example: banks must calculate and store account balances correctly.Authenticity
Confirming the source of data. Example: is an email really from the company CEO?Availability
Timely access to data. Example: necessary information must be available to staff to do their jobs (denial of service attacks seek to disrupt data availability).Utility
Data must be in a useful format. Example: encrypted data is secure but not usable.

|
Yes and no. There's no ITIL certification process offered by ITIL itself. However, an organization that's reached ITIL maturity can generally be ISO 20000 certified. |
Recently on Simplicable

| The Difference Between Public, Private and Hybrid Cloudposted by Anna MarPopular ideas such as cloud computing get twisted, turned and flipped upside down before anyone can agree on common definitions. |

| 5 Levels of Tech Savvy Blissposted by Anna MarModern technology customers and industry insiders are faced with a constant stream of change. Human ability to adapt to this pace of change is remarkable. |

| The 20 People In Your Organization Who Need Enterprise Architectureposted by Anna MarEnterprise architects are leaders. They're near the top of the technical food chain in any organization. As leaders, there are a lot of people in the organization EAs can help. |
















