Web Security Illustrated
posted by John Spacey, March 06, 2013Illustrations of 6 common web security attacks:
1. Distributed Denial of Service (DDoS)
A DDoS attack seeks to bring a website down by flooding it with requests.
DDoS attackers use an array of strategies to paralyse a website. It is common for attackers to:
- tie up network resources such as connections or bandwidth
- tie up server resources such as cpu and memory
- use a zombie army of devices that have been taken over by malware
- focus on layer 4 or layer 7
- exploit vulnerabilities in network equipment
- exploit vulnerabilities in server software and web applications
- use spoofed IPs
- make expensive requests (large files, complex queries etc ...) and then ignore responses
Defences for DDoS include network equipment, specialized hardware and best practices for application development and deployment.
2. Social Engineering
Hacking is a lot of work — in many cases it is easier for an attacker to just call up and ask for information.In one 2003 information security study — 90% of office workers were willing to give up their password for a cheap pen.
Social Engineering starts with a pretext: a lie to gain the users trust. It often ends with the user divulging sensitive information.
Example: An attacker calls a list of users claiming to be tech support. Some users will have a problem with their computers and be happy to divulge passwords or type in commands.

The best defence for social engineering is user awareness and training.
3. Man in the Middle
A form of electronic eavesdropping — two victims think they are talking to each other but both are actually talking to an attacker.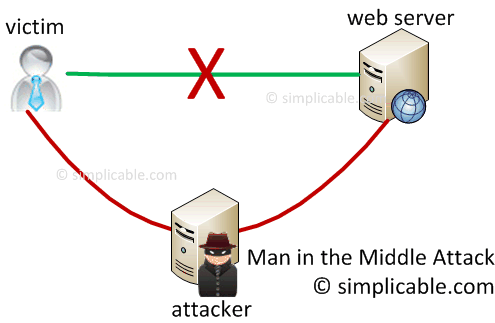
Man in the middle attacks are often used to:
- steal sensitive information from both victims
- execute fraudulent transactions
- inject advertisements and spam
Secure cryptography and strong authentication can prevent most man in the middle attacks.
4. Phishing
Phishing attempts to steal sensitive data by masquerading as a trust worthy website.
The best defence for phishing is user education and tools to warn users of phishing websites. Fighting other attacks such as spam, malware and dns poisoning is also key.
5. SQL Injection
SQL injection is an attack that hides database commands in user input. Attackers submit combinations of special characters and SQL specially designed to trick a website into executing database commands.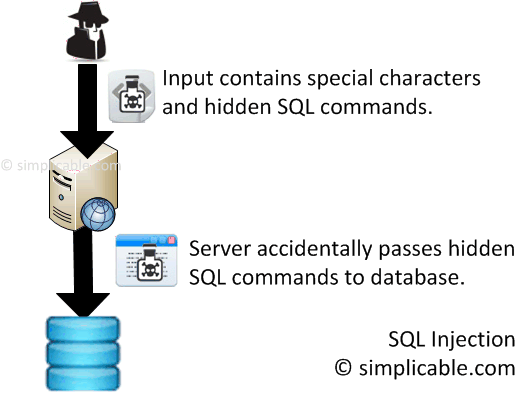
SQL Injection can be avoided with properly implemented user input validation or escaping.
6. DNS Poisoning
DNS poisoning targets services that translates domain names to IPs. The goal is to send users to the attacker's IP when they request a website or service.
DNS Poisoning is often used to steal data, spread false information or vandalize websites.
DNS Poisoning can be prevented by ensuring the security of root and cache DNS servers and local caches on host machines. There is also a cryptographic extension to DNS (DNSSEC) that provides origin authentication of DNS data.
 IT Security Guide
A guide to information security including cheat sheets, best practices and checklists.
IT Security Guide
A guide to information security including cheat sheets, best practices and checklists.
|

|
Ever wonder when that hot new technology is going to get cheaper? Learn what really drives technology prices. |

|
Yes and no. There's no ITIL certification process offered by ITIL itself. However, an organization that's reached ITIL maturity can generally be ISO 20000 certified. |
Recently on Simplicable

| 8 Enterprise Architecture Risksposted by Anna MarEnterprise Architecture (EA) is supposed to help manage IT risks — but is it possible that EA itself introduces new risks? |

| Security Through Obscurityposted by Anna MarSecurity through obscurity is generally considered a bad idea ... |

| IT Security Guideposted by John SpaceyA guide to information security including cheat sheets, best practices and checklists. |















